Use Two-Factor Authentication
- Passwords alone are no longer enough to protect our information and
accounts.
- Two-factor authentication hugely improves your security while causing
minimal inconvenience for you.
- It typically uses time-limited codes – found in an app on your phone –
or a request for approval on another of your devices.
- Two-factor authentication (2FA), two-step verification (2SV) and
multi-factor authentication (MFA) all refer to the same thing.
The problem with passwords
For many years we’ve used passwords to prove our identity when logging into
apps and websites. The idea is, of course, that since your passwords are
known only to you, your accounts and data are kept private.
And this remains generally true: in order for someone else to get into one
of your accounts, they’d need to know your password. The trouble is, this
isn’t as unlikely as you might think.
As you learned in the previous chapter, the secrecy of a password can be
compromised in several ways:
- You might be tricked into disclosing it by phishing. That’s where you
receive a message that appears to be from a service you trust, but is
actually fake, and leads you to a fake page that asks for your password
and sends it to the criminal responsible (for more on phishing, see
Recognise Social Engineering).
- Someone might guess it or, more likely, use software that automatically
makes millions of guesses until one is correct.
- It might be leaked in a data breach. That’s where someone breaks into a
company’s customer database and makes a copy of it, possibly publishing it
for others to find (see Accept That Data Breaches
Happen).
- A kind of malware called a keylogger might end up on
your computer. It records everything you type, including passwords. To
learn how to avoid malware, see Only Open
Trusted Apps and Files.
So, as we depend increasingly on online transactions, and store more of our
data in the cloud, the idea of only a humble password standing between
hackers and our private information is worrying.
In summary, it’s not that passwords don’t do what they’re meant to — it’s
that the chance of a stranger obtaining one of your passwords, and the
consequences if they do, create an unacceptable risk.
Second factors
With two-factor authentication (2FA) in place, your
password is only half of what you need to log into an account. You also need
a second factor, such as:
- A code displayed in an app, typically on your phone.
- A code received in a text message (SMS) or email.
- A code read to you by a computerised voice that calls you.
- A prompt on another computer, tablet or phone that’s already logged
into the account.
- A small gadget, like a memory stick, that plugs into a USB port.
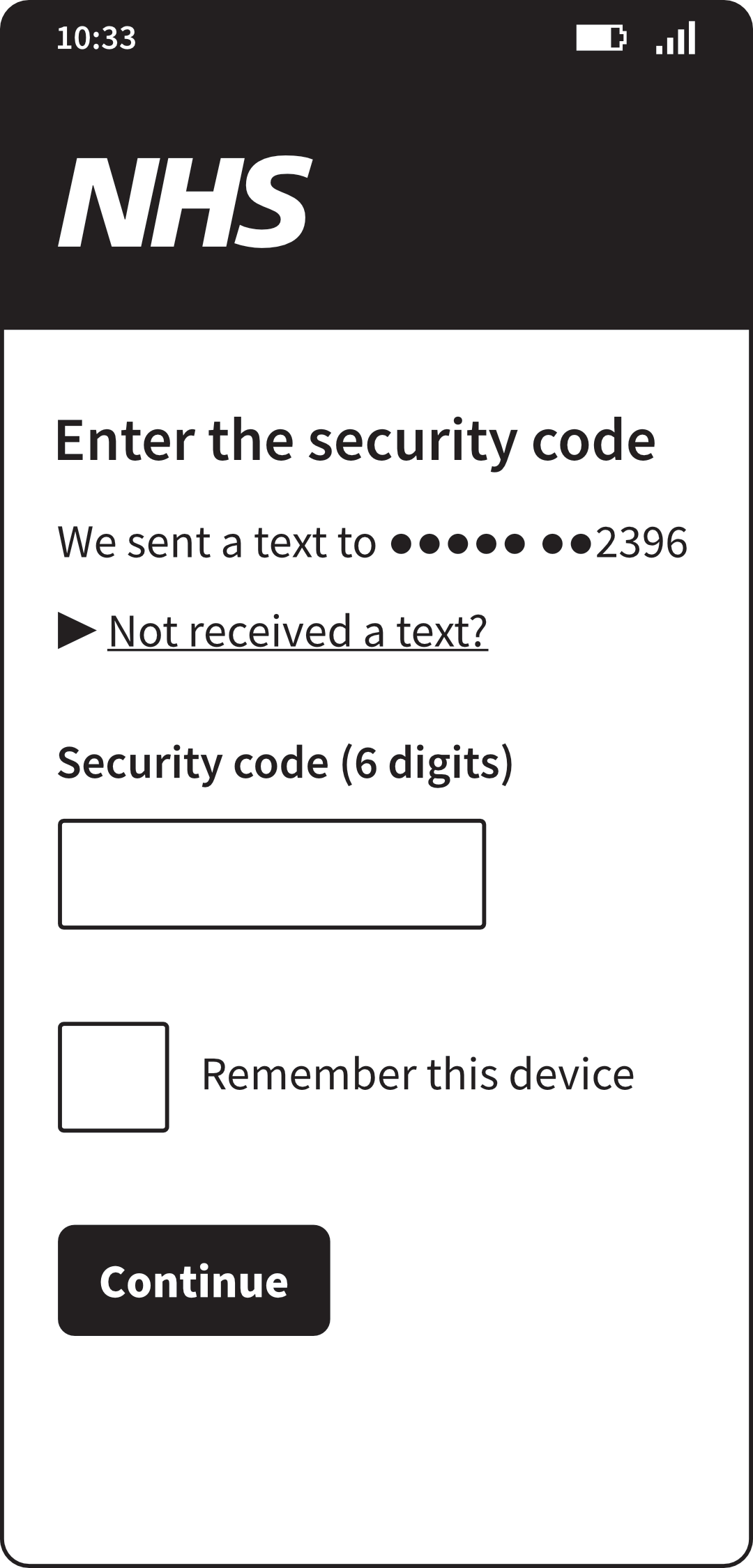 Logging in with two-factor authentication
Logging in with two-factor authentication
Each of these has advantages and disadvantages. For example, text messages
are really easy, but sometimes you’re in a place where you can’t get a phone
signal; and in rare cases, they can be intercepted. A USB device works
anywhere, but is tiny and easy to lose if you’re not careful.
Authenticator apps
A good balance of usability and security can be had with an app on your
smartphone called an authenticator:
- It generates codes internally, so it works even without signal.
- You most likely already have a phone, so there’s no new expense.
- If you lose your phone, a stranger can’t use it because they don’t have
your PIN, fingerprint or face.
Choosing an app
Many authenticator apps are available, but you only need one because almost
all websites use a common standard. For example, Microsoft Authenticator
isn’t limited to making codes for your Microsoft account: you can add your
Google account too, and others like Amazon and Facebook. Equally, Google
Authenticator can make codes for your Microsoft account and more.
Setting it up
Adding your various accounts to your authenticator app can be quite
tedious, so I recommend doing it over a period of days or weeks. Your email
and social media accounts are most important, because they’re valuable
prizes for hackers, so do those first:
- Visit the website on another device, like a computer or tablet, and find
the page for managing your account. The link is typically in the top-right
corner, with an icon of a person’s head, the initial of your name, or your
profile picture.
- Find the option to turn on two-factor authentication. It should be under
a heading like ‘security’ or ‘sign-in options’. Some websites call it
two-step verification (2SV) or multi-factor authentication (MFA).
- Choose the option to use an app, and the website will show a QR code. In
the authenticator app on your phone, go to add an account, and scan the QR
code with your phone’s camera.
- A short numeric code appears on your phone, and the website (on your
computer or tablet) asks you for it. Type the code into the space provided
to confirm that the account is working with your authenticator.
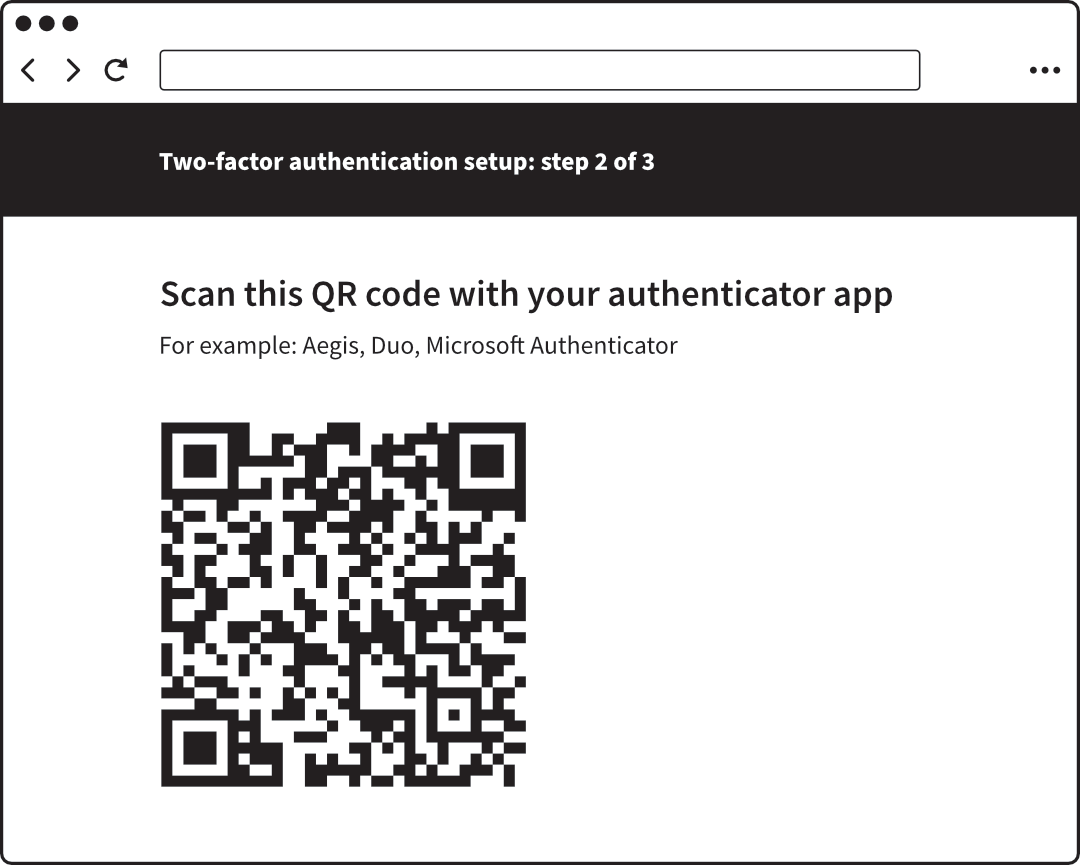 A website showing a QR code to scan with a mobile phone to set
up two-factor authentication
A website showing a QR code to scan with a mobile phone to set
up two-factor authentication
Logging in
When you return to log in the same website in future, it will first request
your password as normal. Then it will ask for the code currently displayed
in your authenticator. This changes periodically, usually every thirty
seconds.
The code must be used within a certain amount of time – though there’s a
leeway after it changes, if you haven’t finished typing it – and each code
can be used only once. In fact, its proper name is a
one-time password (OTP) or one-time
passcode.
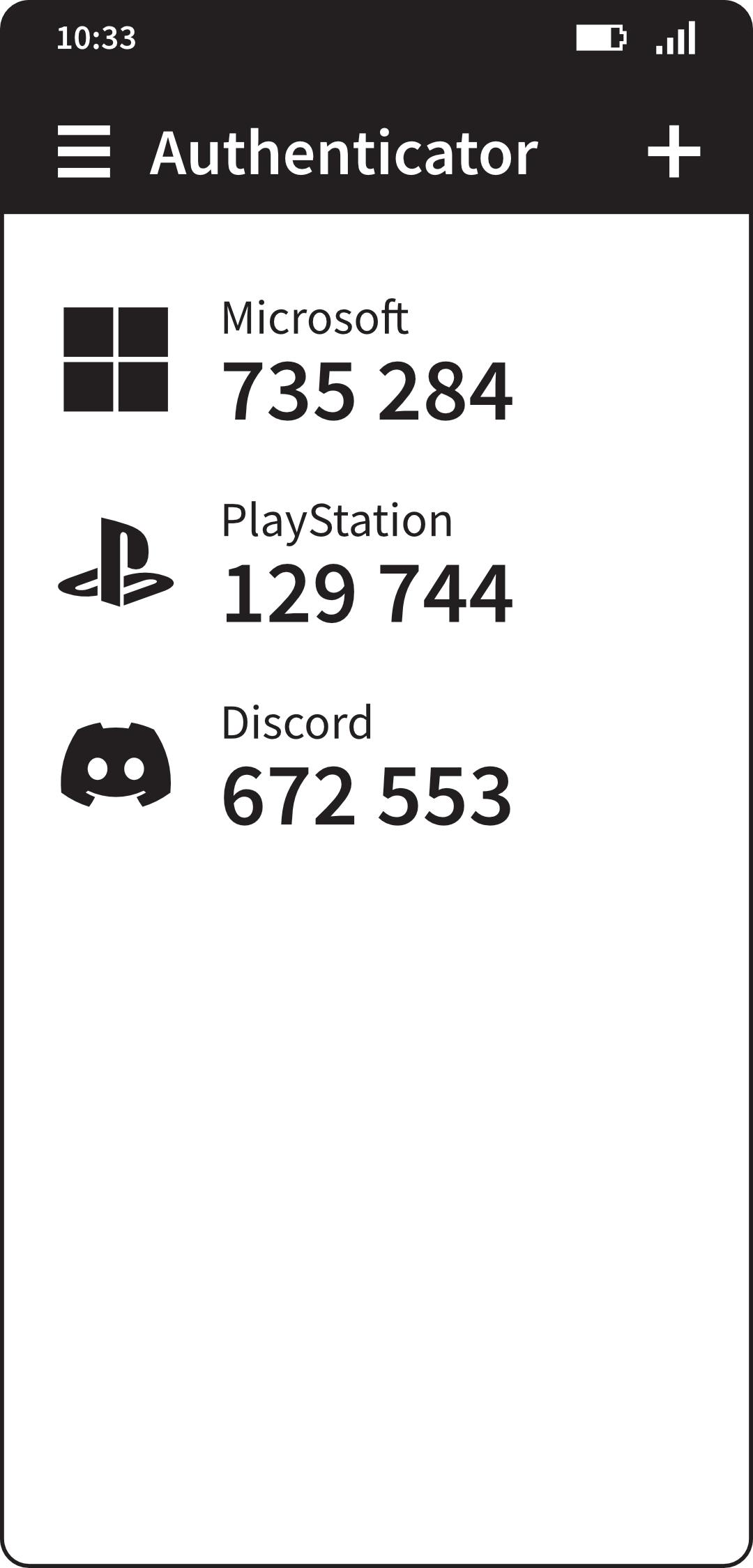 Authenticator app with three accounts configured
Authenticator app with three accounts configured
Authenticator apps generate codes mathematically based on the
current date and time and a longer, pre-agreed secret that was passed from
the website to your phone via the QR code. To allow for inaccurate clocks,
it usually doesn’t matter if you enter a code that’s very recently lapsed
or, if your clock is fast, one that’s been generated a bit early.
Trusted devices
A site may offer to remember or ‘trust’ your particular computer, tablet or
phone so you don’t suffer the inconvenience of two-factor authentication
every time you log in. In fact, on a device used only by you, there’s no
need to ever log out of your email or other accounts — provided the device
itself is locked with a password or PIN when unattended.
So it may be the case that you rarely get asked for an OTP. Your account is
still protected, and if someone tried to break into it from a
different device, they’d be thwarted by the two-factor
authentication — even if they knew your password. This is the ideal kind of
security: minimum fuss for you, and maximum frustration for criminals.
Another benefit of trusted devices is that you can sometimes use one to
authenticate another. For example, if your phone runs the Android operating
system and you also buy an Android tablet, the phone might show a question
like ‘Are you trying to sign into a tablet right now?’ and you can choose
‘Yes, it's me’, skipping the need for an OTP or even your password.
Alternative second factors
Not everyone has a smartphone, and it’s likely that for the foreseeable
future most services will continue to offer text message or phone call
verification as a second factor.
In fact, even when you do use an authenticator, it’s common to register
your phone number with a website so that if your app is unavailable you can
still perform two-factor authentication. The principle is the same, but the
OTP is sent to you via text message or read to you in a voice call.
Recovery codes
As a final precaution against getting locked out of your own account, many
services also offer a printable recovery code or codes. Keep these safe with
other important paperwork, so you know where to find them in the hopefully
unlikely event that you lose your phone and can’t get an OTP via any
method.
What you can do
- Enable two-factor authentication on your email account. It’s your most
important account, because not only does it contain a great deal of
information about you, but a stranger with access to your email can in
turn gain access to your other accounts via their ‘forgotten password’
facility.
- Ideally, enable two-factor authentication on social media and other
accounts that offer it.
- Don’t rely on just one second factor, especially for important accounts.
If possible, register multiple phone numbers as well as an authenticator
app. You could use the phone number of a close friend or family member —
but check with them first, and note that they’ll need to be present to
receive an OTP during the registration.