Only Open Trusted Apps and Files
- Harmful software, called malware, is spread mostly via websites and
email — disguised as something legitimate.
- You can avoid most malware by learning to distinguish genuine websites
from bogus sites, and by not opening unexpected email attachments.
Viruses and malware
Software is what makes computers so flexible and adaptable. Your device is
capable of great things that haven’t been invented yet! But it will just as
readily follow instructions that aren’t well-intentioned.
Software that purposefully compromises your privacy, damages your data, or
uses your device to perpetrate unlawful activity is called
malware.
Note that while people often say virus, a virus is
actually just one kind of malware. True computer viruses, which can
self-replicate, are relatively rare. Malware is the right word to use if
you’re talking about harmful software in general.
We saw in Update Your Software that vulnerabilities
in apps can create ways for malware to get into your computer, tablet or
smartphone, and that keeping your software up to date is the best possible
defence against this avenue of attack.
But you can also install malware directly. Of course, you wouldn’t do this
on purpose! You must be tricked into running it — but how?
Fake websites
People often encounter malware while trying to install genuine software.
Be aware that when you search the web, for example with Google or Bing:
- The first result will not necessarily be the official website.
- A rogue outfit might have paid to place an advert for their own
similar-looking site.
When downloading software from the web, be sure to visit the website of
whoever makes it.
The best way to tell you’re on an official site is to check the URL
displayed in your browser (see Appendix: Understand
URLs). For example, if you’re downloading Adobe Acrobat Reader and the
URL shows you’re on adobe.com, you might reasonably
assume that is Adobe’s official website (which indeed it is).
Fake apps
Software is increasingly available via app stores, like
the App Store on Apple Mac computers or the Microsoft Store on Windows. On
the iPhone and iPad, the App Store is the default way to install apps; while
Android phones and tablets typically have the Google Play store.
Developers must meet certain conditions to make their apps available this
way, and the stores perform checks on the apps they deliver. But the
curation isn’t perfect, and it’s not uncommon to find apps that:
- Show unwanted or excessive advertising.
- Try to steal your private information.
Broadly speaking, these apps either:
- Impersonate popular apps, hoping you’ll install them by mistake.
- Claim to offer a utility, like a calculator or torch.
A fake or rogue app will often ‘work’, in the sense that it will do the job
you expect, in addition to causing annoyance or harm. There may be no overt
signs that anything is wrong. So, your best defence is to avoid such apps in
the first place.
 Sponsored placement of a fake app in an app store
Sponsored placement of a fake app in an app store
Before installing an app, check:
- The name. A fake app might use different or extra words, like ‘Wikipedia
Browser’ rather than ‘Wikipedia’.
- The developer’s name. For example, the App Store page for WhatsApp shows
it is made by WhatsApp Inc. It’s unlikely that a bogus developer could
have registered this name.
- Reviews and ratings. For example, at the time of writing, WhatsApp has
been rated an average of four-and-a-half stars by 200 million users of the
Google Play store. It’s unlikely a fake version would have achieved
that.
Finally, when using an app you’ve installed, be cautious if it requests
permissions that don’t make sense. One great thing about
modern operating systems is that they can grant access to specific data,
like documents or pictures, and specific abilities, like taking photos or
making calls, on a per-app basis. So, if your phone suddenly tells you your
Soduko app wants permission to read your text messages, you can become
suspicious, say no, and get rid of it!
Rogue security software
Ironically, some malware presents itself as software that will
protect you from malware. You might be told: “Warning! Your phone
is infected with five viruses! Tap here to clean it.”
But what you’re actually seeing is just an ‘advert’ on a web page. It
knows nothing about your device, and every visitor sees the same fictitious
message.
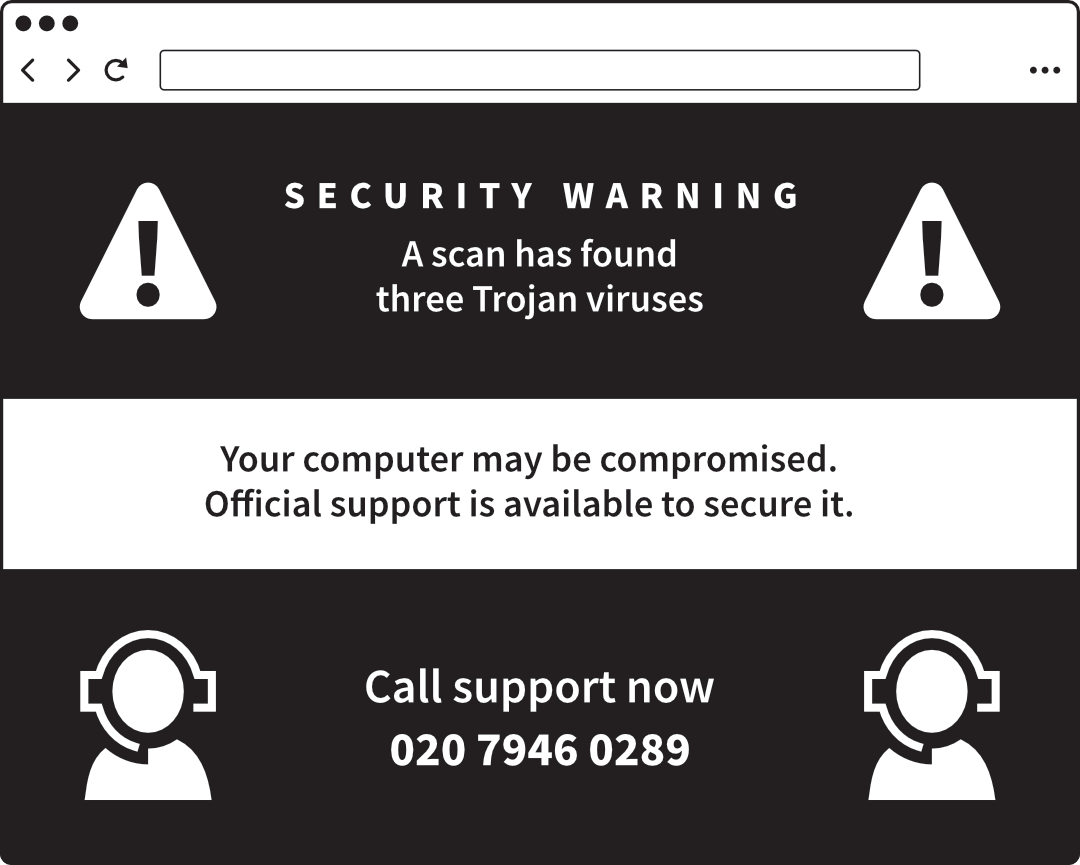 A rogue web page pretending you have a security
problem
A rogue web page pretending you have a security
problem
Three ways to recognise these bogus warnings include:
- They convey a sense of disaster and urgency. Some play a recorded voice
saying your computer is infected. A genuine warning would not be so
dramatic.
- They give you a phone number to call. Real security software doesn’t do
this.
- Because the warnings are really just web pages, they appear contained
within your browser. If you close the browser, the warning will disappear
with it.
No harm will have come from you seeing this hoax. You’d only be in danger
if you followed up on what it was suggesting, like installing an app or
calling a number. Otherwise, you can ignore it and carry on your day.
If you can’t get the warning to go away, try restarting your device. If
you’re stuck, try asking a friend to help.
Malicious emails
Although email is one of the oldest means of distributing malware, it is
still used today. In fact, one of the most serious kinds of malware, called
ransomware, is often spread this way (for more on ransomware, see
Back Up Your Data).
Emails can deliver malware in two ways:
- Attachments. Malware may be disguised as familiar file types like JPEG
or PDF. Thankfully, modern email services scan attachments for malware and
block a significant proportion of it. Still, as a rule, if you’re even
slightly unsure about a file you’ve received, don’t open it.
- Links to websites. Instead of attaching it directly, an attacker may
email a link to a website where a harmful file is presented for download.
One trick is to show a page that pretends you need to install an update in
order to view the message; the ‘update’ is actually malware.
Note that it’s virtually impossible to harm your device by merely viewing
an email. So, if you accidentally opened a suspicious email, but didn’t open
any attachments or click any links, you needn’t worry.
It’s easy to ignore and delete messages that are blatantly unsolicited.
What’s harder is spotting bogus communications that impersonate a friend or
a company you deal with. Means of verifying the authenticity of messages,
and the risk of disclosing sensitive information through phishing, are
covered separately in the next chapter,
Recognise Social Engineering.
Antivirus software
Modern devices are designed with security in mind, and multiple defences
must be breached for a computer to be seriously harmed. The importance of
one of these layers has long been exaggerated: antivirus
software.
Note that in this case, ‘antivirus’ really means ‘antimalware’ — such
software doesn’t exclusively target viruses. But ‘antivirus’ remains the
more common term, for historic reasons.
I find that people often talk about antivirus software like it’s their
first line of defence — even a panacea. Naturally, years of good marketing
by antivirus vendors has helped create this impression.
How it works
Central to most antivirus software is a database of known malware. As new
kinds of malware are discovered, the vendor creates
definitions for them, and adds these to the database.
Whenever you download or open a file, the antivirus checks it against its
database. If there’s a match, it blocks the malware from running. This
on-access or real-time checking means you
don’t need to regularly scan your whole computer for malware.
The limitation of this approach is that the people creating malware are
always ahead of the antivirus vendors. New malware appears every day. To
help combat this, modern antivirus software also looks for suspicious
characteristics in files and apps, as well as exact matches with its
database. This heuristic analysis is necessarily imprecise,
so it may sometimes result in a false positive, in which
the antivirus unwantedly blocks a harmless file.
An additional challenge is that because it must be embedded deep within the
operating system, glitches in antivirus software can break other apps or, in
rare cases, make your computer less secure.
You now know the basics of how antivirus works, and its strengths,
weaknesses and limitations. You’ve learned that antivirus is not a silver
bullet, and that you should think of it as just part of the overall picture
when it comes to computer security. If anything, consider it your very
last line of defence.
Built-in antivirus
Both Windows and macOS have built-in antivirus software that works quietly
in the background to help protect your computer. Free and commercial
third-party antivirus products may claim to provide superior protection, or
score more highly in lab tests and reviews, but you should not assume they
will be more effective than built-in antivirus in real-world use.
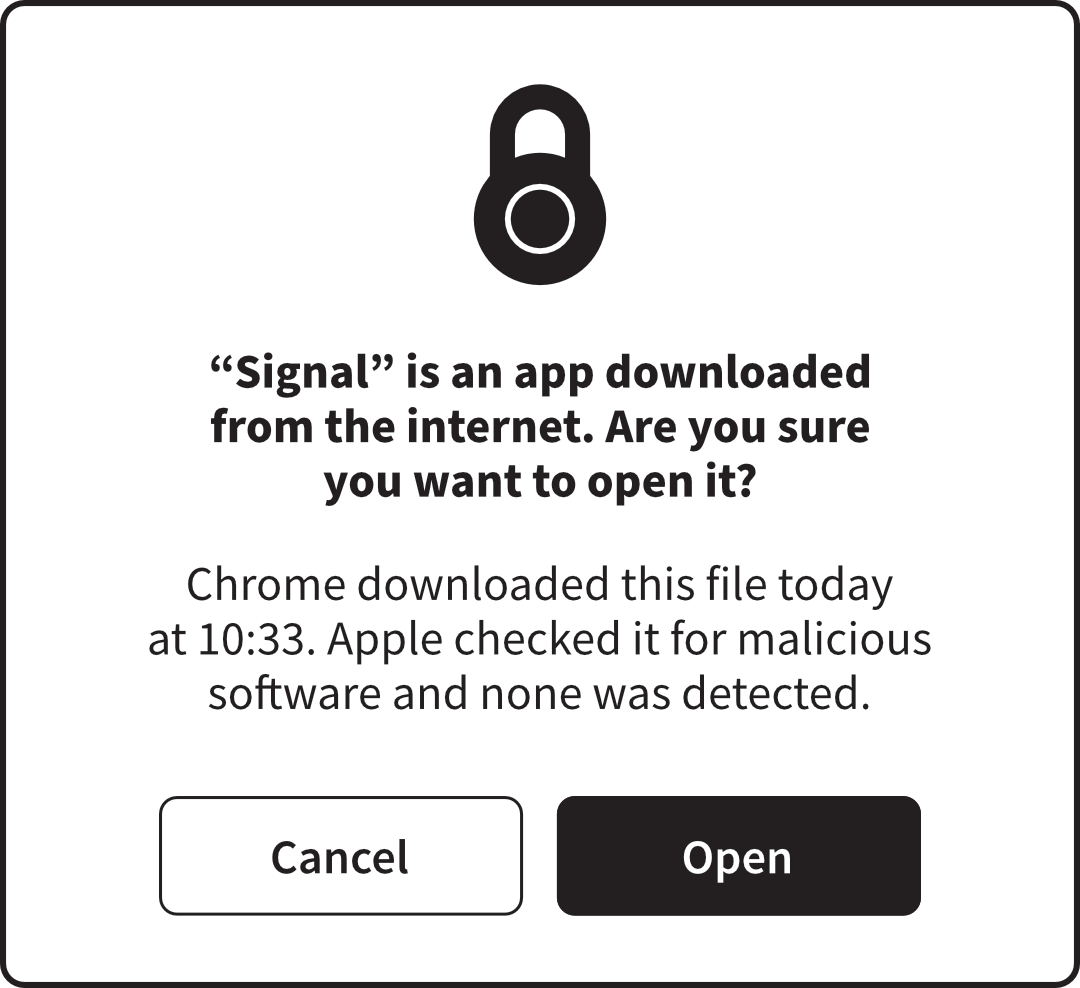 Built-in antivirus giving the all-clear on opening a new app
for the first time
Built-in antivirus giving the all-clear on opening a new app
for the first time
Tablets and phones
Tablets and smartphones run operating systems that have been designed more
recently, and take into account knowledge gained from years of experience
securing computers. Apple and Google have been able to make bold decisions
about the way these devices work, and their limitations — because they are
not expected to be as comprehensive as traditional computers, or provide
compatibility with decades-old business systems.
In particular, iOS and Android segregate individual apps from each other
and from the inner workings of the system. This means not only that tablets
and smartphones are much less likely to be infected by malware, but that
third parties cannot produce traditional antivirus software for them.
So, if you’re wondering whether you need an antivirus app for your tablet
or smartphone, the answer – in a nutshell – is no.
The same is true for Chromebooks, for the same reasons.
What you can do
- Use caution when installing software from websites. Be sure to obtain it
from a trusted source, like the developer’s own website.
- Install software from app stores where possible. The Microsoft Store on
Windows; the Apple App Store on Mac, iPhone and iPad; and the Google Play
Store on Chromebooks and on Android tablets and phones are curated to
reduce the likelihood of harmful software being available.
- Check an app’s name and the name of its developer, along with its
rating, to avoid installing fake or malicious apps.
- Ignore websites that say your computer, tablet or smartphone is in
danger. They’re not real.
- Beware of bogus emails impersonating people or companies you trust.
Never open an unsolicited attachment, and use caution with links.
- Modern computers, tablets and smartphones are designed with security in
mind. You don’t need to install additional security software.